WAYDEV SECURITY
Security is our top priority! SOC 3 Certified
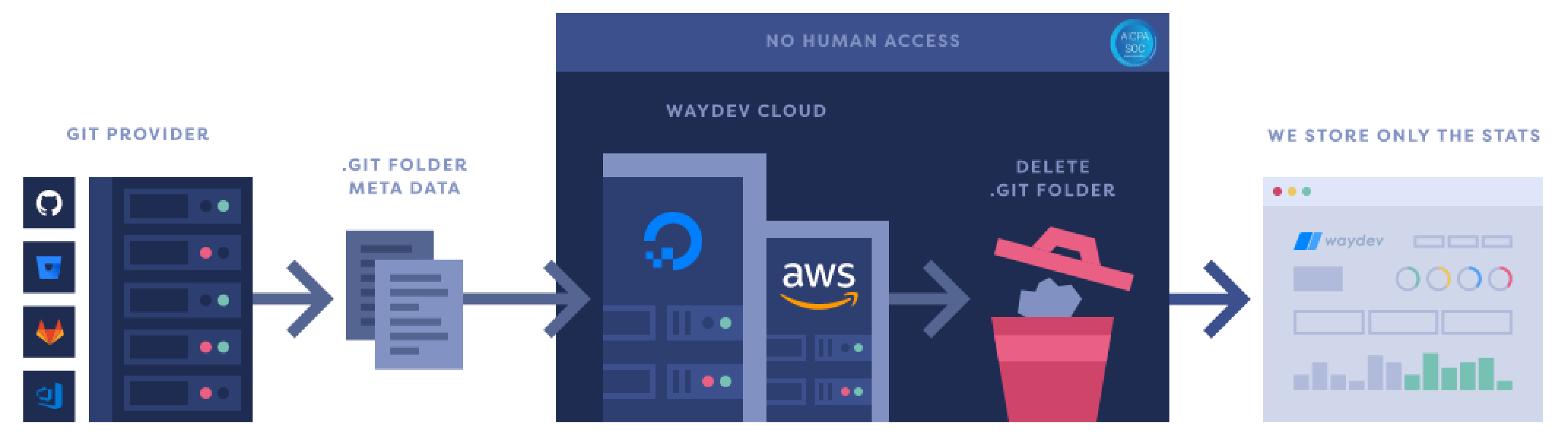
Your security is critical to us, we have the highest level of security (SOC 3)
We do not store any copies of your repositories

We are SOC 3 compliant
Highest level of trust and transparency
We always connect via your Git provider tokens
When you disconnect your repositories, all associated stats are purged from the system
ALL DATA IS TRANSMITTED OVER A SECURE PROTOCOL
Our code only interacts with GIT providers using temporary token credentials that we refresh frequently
Highly secure payments
We use Stripe for all credit card and payment information processing
READY TO ADOPT A DEVELOPER PRODUCTIVITY INSIGHT PLATFORM?